Lockphish: A Tool For Phishing Attacks On The Lock Screen
- How to SPY on someone with a Man in the Middle Attack(MITM)?
- How to reset root password in Kali Linux?
- How to File a Cyber Crime Complaint in India | Cyber Crime Reporting Portal
- Cyber Laws (IT Law) in India | Everything about Indian Cyber Laws
- 5 Attacks Which are Harmful For Your Whatsapp Account & How to be safe in 2020!
- How to Secure Your Computer with follow Simple Tips 2020
- Why Hacker use Nodistribute Site instead of Virustotal for Scanning Virus and Malwares
- How to Detect Hidden Camera Using Android Phones | The Secrets to Finding Hidden Cameras
Disclaimer: The usage of Lockphish for attacking targets without prior mutual consent is illegal. It’s the end user’s responsibility to obey all applicable local, state, and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
Features:
- Lock screen phishing page for Windows, Android, and iPhone.
- Auto-detect device.
- Port Forwarding by Ngrok.
- IP Tracker.
How to perform Lock Screen Phishing Attacks using Lockphish Tool
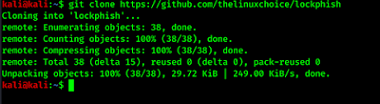
git clone https://github.com/kali-linux-tutorial/lockphish
After writing the command on the terminal window. it will start the cloning process as shown in the following screenshot.
STEP2: After finishing the process, You need to go to LockPhish directory by using the below command, and hit the enter key.
cd lockphish
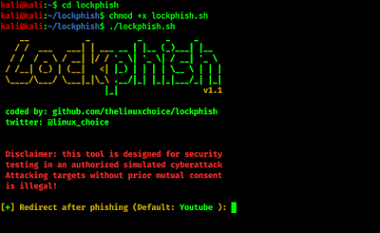
STEP3: Now, the next important thing, you need to give lockphish executable permission before the run. To do that you apply the following command:
sudo chmod +x lockphish.sh
STEP4: After giving executable permission, Then you need to run the tool by using the following command, and hit enter key.
./lockphish.sh
STEP5: Now, the main menu of LockPhish will open as showing in the following screenshot:
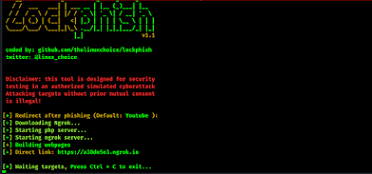
STEP6: After that, you put the redirecting website’s link after phishing. The default value is set to YouTube. YouTube is good for social engineering or, you can put other links also. Here, for example, you keep it default and hit the Enter button.
STEP7: Now, it will download ngrok in your Kali Linux machine, and configure the phishing servers on our localhost, and finally give us the Phishing URL.
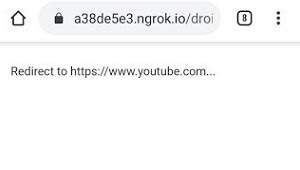
STEP8: After that, you can send this link to your target victim with some social engineering techniques. When your target victims open this link then, it will ask to redirect on YouTube Website.
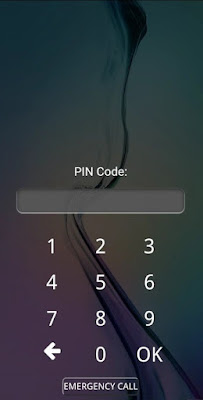
STEP9: When your victim clicks here to be redirected on YouTube, the device shows the following kind of screen:
STEP10: After your victim inputs, his Unlock PIN you got it on your terminal window of Kali Linux.